IT Compliance Services

IT Compliance Services to Meet Regulatory Requirements
Ensuring your company is in compliance with regulations often requires outside expertise. Maintaining a strong IT security stance and complying with relevant regulations are separate, but often overlapping, activities.
K3 has IT compliance experts who can:
- Perform gap assessments for organizations to determine what is missing to meet compliance requirements
- Assist in creating policies, procedures and controls to implement and maintain a compliance program
- Explain regulations that impact your organization, such as Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI-DSS), California Consumer Privacy
- Act (CCPA) and General Data Protection Act (GDPR).
- Guide organizations along the way to receiving industry specific certification, including ISO/IEC 27001, Cybersecurity Maturity Model Certification (CMMC), etc.
Benefits of IT Compliance Include:
- Avoid fines and penalties for noncompliance
- Align information security with business processes
- Create a culture of continual improvement for data security
- Improve accountability by better defining responsibilities and duties
- Reduce expenses related to information security incidents
- Improve trust with customers and other external parties by assuring compliance with security requirements
What are the Differences Between Compliance and Security?
IT compliance relates to regulations and ensures a company meets the minimum level of security-related requirements. Depending on the location and industry, a company may have to comply with multiple regulations, so understanding what is needed to adhere to relevant regulations often requires outside assistance. Compliance goes beyond the implementation of security protocols and encompasses risk mitigation, policies, regulations and laws.
IT security relates to a company’s systems, processes and tools that are in place to protect data, technology assets and other resources. An example of a security tool is multi-factor authentication (MFA) , which requires users to provide two or more factors (something you know, something you have and/or something you are) to verify their identities, preventing a bad actor with a single stolen credential from accessing your network. Systems and tools are available for on-premises, cloud and hybrid applications.
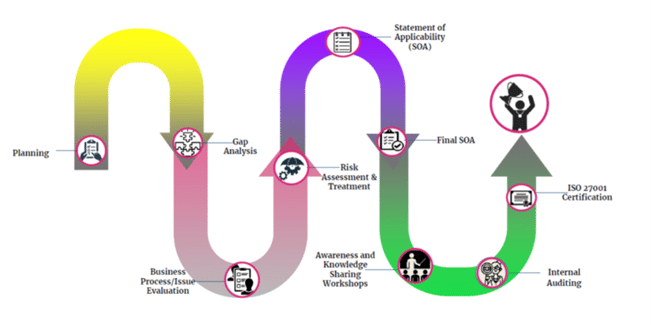
How K3 Helps Companies with Certification
Here’s an example of how K3 works with clients seeking ISO 27001 certification. ISO 27001 provides a framework that can safeguard information assets while making the process easier to manage measure and improve. The international standard allows you to track organization risk, achievement of objectives, KPI reporting, resource allocation, and most importantly, the overall security posture.
IT security and compliance may be separate, but they work together to ensure a company protects its networks and stays in compliance with relevant regulations. Contact K3 today to learn more about our compliance services and security services.
