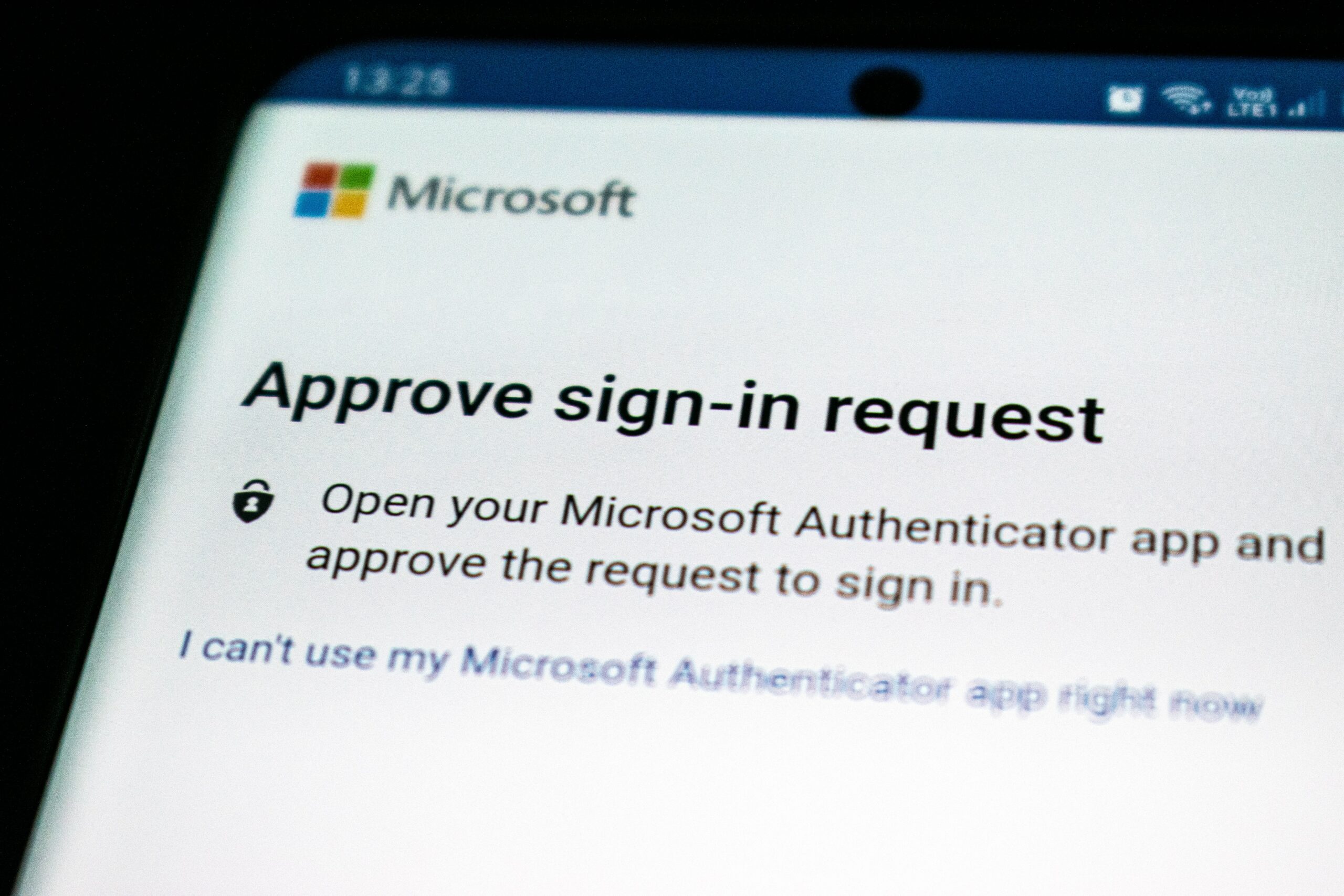
Introduction: What is 2 Factor Authentication and How Does it Work?
In our ever-evolving digital world, safeguarding your online presence is paramount. As data breaches and cyber threats loom, the need for robust security measures has never been more pressing. Enter 2-factor authentication (2FA), a powerful tool in the realm of online security. But what is 2 factor authentication, and how does it work?
2FA is a security method that goes beyond traditional passwords to provide an extra layer of protection. It ensures that only authorized individuals can access your accounts or systems.
2-factor authentication (2FA) works by requiring users to provide two distinct forms of verification to access their accounts or systems. Typically, users are asked to provide something they know (e.g., a password) and use something they have (e.g., a smartphone or a security token).
In this blog, we’ll explore what 2 factor authentication is, how it works, and its benefits.

What is 2-Factor Authentication?
2-factor authentication (2FA) is a robust security measure that fortifies online accounts and systems against unauthorized access. It goes beyond traditional passwords by requiring users to provide two distinct forms of verification before granting access.
The first factor is typically something you know, like a password, while the second factor involves something you have, such as a smartphone or a security token. This dual-layered approach significantly enhances security because even if a malicious actor gains knowledge of your password, they won’t be able to access your account without the second factor.
2FA comes in various forms, including SMS codes, authenticator apps, biometrics, and hardware tokens. Each method offers unique advantages, catering to individual preferences and security needs.
By implementing 2FA, you can depend on a higher level of security that protects your sensitive data.

How Does 2 Factor Authentication Work?
There are several types of 2 factor authentication used for security. Each method is designed to enhance the protection of your digital accounts and data. These diverse authentication techniques cater to individual preferences, technological advancements, and security needs.
By offering a spectrum of choices for 2FA, K3 Technology empowers users to select the 2FA solution that aligns best with their security requirements. Continue reading to learn about the details of each 2FA method.

What is Knowledge-based Authentication?
Knowledge-based authentication (KBA) is one of the key methods within 2-factor authentication (2FA). It involves verifying a user’s identity by asking them questions only they should know the answers to. While KBA is straightforward and user-friendly, it’s important to note its limitations.
K3 Technology offers KBA as an option for 2FA, allowing users to set up security questions and answers. This process can include queries about personal information, such as the user’s mother’s maiden name or the name of their first pet.
However, KBA has its drawbacks. The answers to these questions may be discoverable or guessable, making it less secure than other 2FA methods. Moreover, individuals may forget their answers, leading to account access issues.
Despite these limitations, KBA can provide an additional layer of security when used in conjunction with other 2FA methods, enhancing overall protection for online accounts and systems.

What is Possession-based Authentication?
Possession-based authentication is a fundamental component of 2-factor authentication (2FA), providing an additional layer of security in the digital realm.
This approach requires users to prove their identity by presenting something they possess, such as a smartphone, security token, or a smart card. To access their accounts, individuals must have this physical item in their possession, which makes it significantly harder for unauthorized users to gain access.
While possession-based authentication adds a robust layer of security, it is vital to safeguard the physical item. If lost or stolen, it can pose a potential security risk. Therefore, it’s crucial to combine possession-based authentication with other 2FA methods to create a comprehensive security strategy that offers both convenience and protection. This synergy ensures that your digital world remains secure, mitigating the risk of unauthorized access.

What is Biometric Authentication?
Biometric authentication is a cutting-edge method employed within the realm of 2-factor authentication (2FA). This technique utilizes unique biological or behavioral characteristics, such as fingerprints, facial recognition, or iris scans, to verify a user’s identity.
It is an effective means of ensuring only authorized individuals can access accounts or systems, as these biometric features are incredibly difficult to replicate. Biometric authentication offers a high level of security and user convenience, as there’s no need to remember passwords or carry physical tokens.
However, like other 2FA methods, it has its limitations, such as the need for robust security measures to protect biometric data. When integrated into a comprehensive 2FA strategy, biometrics enhance the overall security posture, ensuring that digital access remains both secure and user-friendly.

What are Time-based One-time Passwords?
Time-based one-time passwords (TOTP) represent a dynamic facet of 2-factor authentication (2FA). This method generates unique, time-sensitive codes for each login attempt, offering an additional layer of protection against unauthorized access.
TOTP relies on a shared secret, typically stored on a user’s device or generated by an authentication app, and a precise timestamp. The time-based nature of these codes means they’re valid only for a short duration, usually around 30 seconds. This creates a constantly evolving barrier to unauthorized entry, as the code changes with each new time interval.
While TOTP provides robust security, users must ensure that their devices’ clocks are synchronized with the authentication server’s time, a critical requirement for the system to work seamlessly. With TOTP integrated into your 2FA strategy, K3 Technology ensures enhanced online security, making it exceedingly difficult for malicious actors to breach your accounts or systems.

What are the Benefits of 2 Factor Authentication?
2-factor authentication (2FA), provided by K3 Technology, offers a multitude of benefits that are essential for safeguarding online accounts and systems.
Foremost, 2FA significantly enhances security by requiring two distinct forms of verification before granting access. This fortifies your defenses against unauthorized entry, even if a malicious actor has obtained your password. It acts as a robust barrier, making it much more challenging for cybercriminals to breach your accounts.
Furthermore, 2FA also offers protection against common password-related attacks, such as brute force and phishing. With the additional layer of authentication, these tactics become less effective, minimizing the risk of account compromise.
K3 Technology’s 2FA solution prioritizes user-friendliness, ensuring a straightforward and secure experience. By adopting 2FA, individuals and organizations can take a proactive step towards a heightened level of online security. Protect your sensitive information and maintain the integrity of your digital assets with 2FA.
Frequently Asked Questions
RELATED TO: “What is 2 factor authentication, and how does it work?”
How does 2FA enhance security?
2FA significantly enhances security by making it much harder for unauthorized individuals to access your accounts. Even if they know your password, they won’t be able to log in without the second factor, which adds a critical layer of defense against cyber threats.
What should I do if I lose my second factor for 2FA?
If you lose your second factor, like a smartphone or security token, most platforms provide backup access methods, such as backup codes or alternate email verification, to regain access to your account.
How does 2FA contribute to data protection?
2FA contributes to data protection by ensuring that only authorized individuals can access sensitive information. It reduces the risk of data breaches, protecting the confidentiality and integrity of digital assets.
Is 2FA suitable for all businesses and individuals concerned about cybersecurity?
Yes, 2FA is suitable for businesses and individuals of all sizes. It offers an extra layer of protection that is essential in today’s digital landscape, making it a valuable tool for enhancing cybersecurity for everyone.
Conclusion: What is 2 Factor Authentication and How Does it Work?
All in all, the implementation of 2-factor authentication (2FA) is a pivotal step in fortifying your online security. 2FA, with its multi-layered approach, offers an effective shield against unauthorized access and cyber threats. By combining something you know and something you have, it forms a formidable defense that safeguards your sensitive data and online assets.
The advantages of 2FA are clear – enhanced security, protection against password-related attacks, and user-friendliness. As the digital landscape continues to evolve, K3 Technology remains committed to ensuring that users and organizations can navigate this landscape securely.
By adopting 2FA, you are taking a proactive step towards safeguarding your digital world. Your online accounts and systems will remain protected, and your data integrity preserved, as we collectively strive for a safer and more secure online environment.